Find Out the Root Cause and Avoiod Reinfection
Introduction

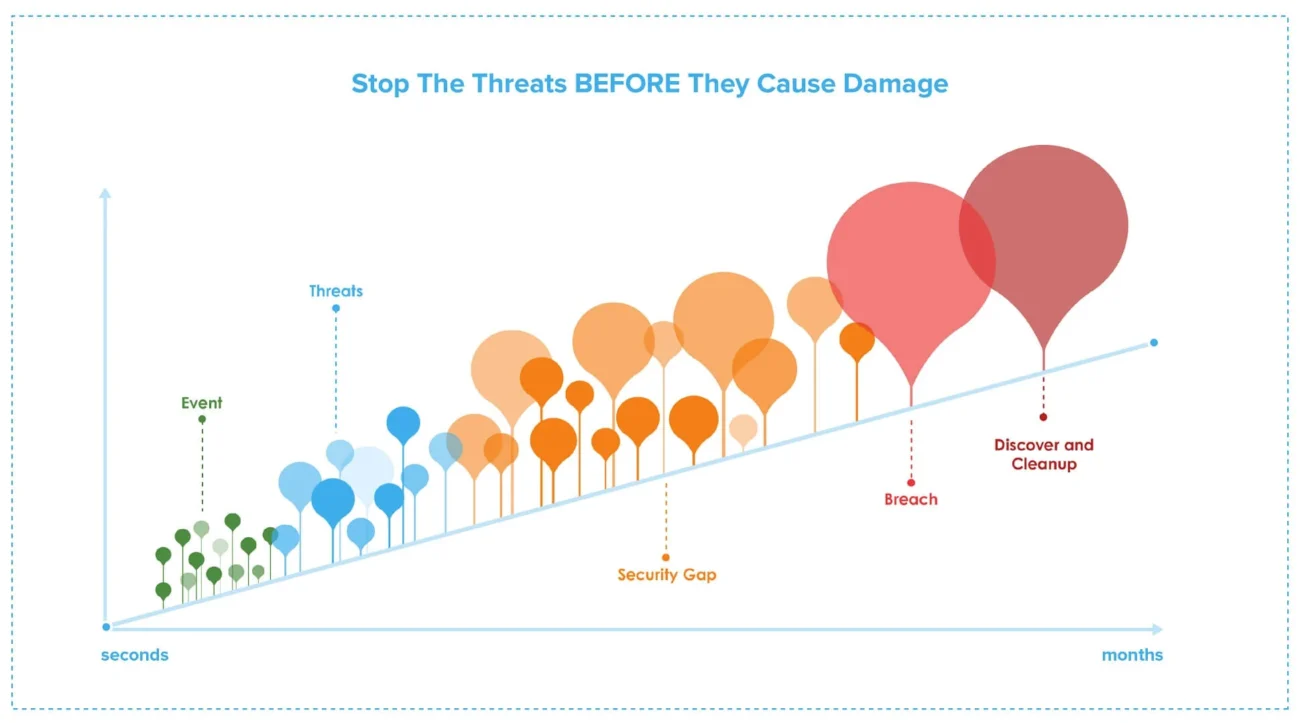
Why you need continuous threat detection
350,000 new malware strains everyday Your existing security controls can only block 99.5% of them. That means 1750 new malware attacks every day can bypass your security devices New malware and virus variants are produced every day. According to AV-TEST Institute, there are over 350,000 new malware samples registered every day. So, you can imagine that if your existing security controls can block 99.5% of the new malware every day, there are still more than 1,750 malware threats that can bypass your security controls and get into your network. Even worse, studies show most threat detection services organizations’ have in place are unable to prevent 50% of the new malwares. This is an alarming figure and should serve as a wake-up call for companies to take appropriate action when it comes to advanced threat detection, implementing network traffic analysis tools, and getting the latest and best threat hunting and detection software available.
Security Teams Need to Shift Mindset
Work from Anywhere Scenario Solutions

aDesk / HCI + Endpoint Secure
- Data never leaves the environment
- Good for medium to large organizations
- Good for smaller organizations especially with MSSP but may be expensive

Cyber Command + SD-WAN / NGAF SSLVPN + Endpoint Secure
More cost-effective option for smaller organizations or those not cloud ready

IAG + Endpoint Secure SWG/CASB
Endpoint risk analysis in addition to Authorization/Access control

Business Benefits
- Compliance auditing
- Ensure authorized users only
- Prevent data leakage

Scheduled or on-demand endpoint Secure vulnerability scanning initiated by NGAF

Vulnerability Scan results sent back to NGAF for closed-loop patch

Real-time Threat Intelligence (TI) from cloud-based NeuralX recognizes malware

Network-Wide Threat Disposal allows the administrator to respond

Cyber Command for enhanced threat detection/response

Vulnerability Scan results sent back to NGAF for closed-loop patch

Enterprise asset tracking and rogue asset detection

Endpoint Secure Protect Agent Ransomware honeypot capability