Secure User Internet Access Behaviour
Accelerating modern trends such as cloud applications adoption, the move of the hybrid workplace and increased use of mobile and personal devices for work have all constantly put more pressure on the organization to ensure a secure workforce environment. At the same time, a rise in encrypted applications, proxy avoidance applications, and increasingly affordable availability of third-party VPN applications have imposed further liability for the organization where it can easily bypass your security perimeter undetected without any protection. You need an extensive secure web gateway not only to protect your organization against these common threats but also as a critical asset for safeguarding user internet access behavior.
Sangfor IAG enables you to identify, analyze and take immediate action upon user internet access behavior.

Gain full visibility to find any bad behavior in encrypted traffic.

Ransomware Protection
Uncover user identity with analytics into who is using what applications and when it is used on your network.
2nd Tier Firewall
Take full control to increase user productivity by ensuring internet access compliance.
Proxy Avoidance Protection
Web filters are commonly used by the organization to restrict user internet access to certain web applications content and it has increasingly become non-effective against proxy avoidance applications. IAG collaborates with Endpoint Secure to enforce Proxy Avoidance Protection on any user attempt to use this application for bypassing the security perimeter more effectively. R&D team within Sangfor employs a dedicated team of application signatures security experts who are continuously categorizing and adding the latest proxy avoidance applications to ensure that detection rate and blocking capabilities are current and up to date.
Intelligent Traffic Management
Sangfor IAG improves bandwidth utilization by more than 30% using three unique major traffic management solutions. Dynamic Traffic Control automatically adjusts traffic control policies and intelligently allocates idle bandwidth resources. Intelligent Flow Control precisely manages both up-link and down-link P2P traffic and can customize traffic “packages” for different users, allocating specific traffic quotas and limiting bandwidth for heavier users.
Gateway and Client Decryption to Uncover Encrypted Traffic
Typically, a majority of internet traffic is protected by SSL/TLS encryption. While encryption helps to keep user and corporate data protected and private, it also creates security challenges when it comes to the rapid growth of malware infections and other malicious content. Sangfor IAG offers both decryption methods including gateway and client decryption to overcome these challenges. This enables an organization to have the flexibility to run either one or both in parallel to uncover encrypted traffic according to your corporate IT strategy and planning.
Unified Network-wide Management of all Clients
Sangfor IAG provides Unified Management and effectively controls both Wired and Wireless networks for the entire network. With intuitive and flexible authentication methods, it fully guarantees the security of access control, supporting a variety of traditional authentication methods such as username/password, IP/MAC binding, and a wide array of value-added marketing authentication methods (QR code, SMS, WeChat, Social media, OA account, SAML 2.0, third-party system, etc.). Permissions are controlled based on user, application, location, and client types while using IAG or third-party wireless controller as a unified authentication server, building a faster and more cost-effective wireless network.
Precise and Accurate Application Control
Sangfor IAG manages and controls network applications more comprehensively, accurately, and conveniently with the largest application signature database in Asia, which can identify more than 6,000+ applications in its database including 700+ cloud applications, 1,000+ mobile applications, 300+ web applications, and is updated every 2 weeks. In addition, it precisely controls applications according to their specific functions, such as distinguishing upload, download, and other actions in the network. Finally, bulk management mode for large enterprises greatly improves management efficiency.
Gateway and Client Decryption to Uncover Encrypted Traffic
Typically, a majority of internet traffic is protected by SSL/TLS encryption. While encryption helps to keep user and corporate data protected and private, it also creates security challenges when it comes to the rapid growth of malware infections and other malicious content. Sangfor IAG offers both decryption methods including gateway and client decryption to overcome these challenges. This enables an organization to have the flexibility to run either one or both in parallel to uncover encrypted traffic according to your corporate IT strategy and planning.
Offloading Performance When Using ICAP Integration With Third Party System
Sangfor IAG can act as an ICAP client to be used with any ICAP server-enabled network appliance by offloading threat protection or other value-added services. In addition, Sangfor IAG provides request and response inspection mode while enabling the ICAP server group to run on a round-robin or concurrent condition.
Secure Onboarding Devices With Endpoint Security Posture
Sangfor IAG identifies and secure endpoint devices with or without agents, it helps to ensure these devices are connected with compliant and secure. You gain visibility and control what is on your environment without impacting your network performance.
Below you will find all the Success Stories with Secure Internet Gateway, classified by Industry, such as Enterprises, Governments, Schools & Universities, etc.
Advantages: Making Cyber Threat Hunting Simpler
Sangfor’s Cyber Command offers a host of advantages for clients for cyber threat hunting and threat detection
Without Sangfor IAG the office environment is comparable to an internet cafe where users and staff can freely access video, social media, and endless entertainment. IT administrators are hard-pressed to identify exactly which users are consuming excess bandwidth, preventing effective control over user browsing behavior. Sangfor IAG can identify and control non-work-related applications in the network while allowing companies to keep a close eye on their bandwidth management, whereby they allocate all available bandwidth for key business needs, and improving business efficiency and productivity. Numerous professional traffic management features allow IAG to rationally allocate bandwidth resources and maximize bandwidth usage. For organizations with multiple branches, IAG provides a unified management platform and supports 3G link backup, making network management more efficient and reliable.
Because customers have vastly different authentication procedures, each internal network requires user authentication integration with AD, Radius to achieve SSO. IAG guest authentication provides convenient access through Facebook, WeChat, SMS and offers a unified authentication solution, which manages both the wired and wireless connected users within a single IAG platform. Sangfor IAG also offers a switch based user access control capability to help control LAN user access. Finally, Sangfor IAG can be integrated with WLAN vendors like Cisco, Aruba to allow the Unified Authentication Center to drastically simplify the process of network integration and management.
To protect the user from web threats, a secure web gateway is an effective defense over web-based threats and enabling secure internet access. Sangfor IAG can work with your on-premise applications and internet traffic. With the accelerated SSL decryption performance, all HTTP and HTTPS traffic will be monitored and analyzed with IAG, which is the huge bottleneck of other solutions like NGFW or UTM. The AI-based threat intelligence platform provides web filtering services and improves the capability of identifying known and unknown threats. It also keeps users protected while ensuring they enjoy a safe and secure web experience.
As unauthorized use of networks becomes more common, many countries and regions are developing and enforcing laws governing user internet access behavior. The IAG internal application database comprehensively logs malicious user activity including file uploads, BBS posting, email, browsing history, and applications accessed. This audit solution assists in customer compliance with local legal regulations and serves as a valuable investigative resource in the event of illegal network usage incidents.
Secure Playlist
Sangfor Network Secure Brochure
Sangfor Network Secure Datasheet for the Model NSF-3100A-I
Sangfor Network Secure Datasheet for the Model NSF-1100A-I
Sangfor Network Secure Datasheet for the Model NSF-1050A-I
Secure Internet Gateway Frequently Asked Questions
Please perform it following:
- Step 1. Add a new LDAP Server under the External Auth Server.
- Step 2. Enter the details such as Server Name, IP Address of the external authentication server, the admin account username and password and select the BaseDN. After entered all the details, click the Test Validity to check whether able to connect the external authentication server or not.
- Step 3. After tested the validity, a message will prompt out to show the result.
- Step 4. Click the Sync with all LDAP servers to sync all the data. Now, the configuration is successfully set.
In a typical environment, Secure Web Gateway (SWG) is used to block access to inappropriate websites or applications, prevent malware infections, and enforce corporate internet compliance. SWG is similar to a firewall in that both prevent malicious activities and provide necessary network security protections. However, the main difference is that SWG emphasizes securing user onboarding and promoting productivity. It is common for an enterprise to use both SWG and firewall to fortify their defense as both of them usually complement each other. For more info on using both Sangfor IAG and Network Secure, please refer to this blog webpage.
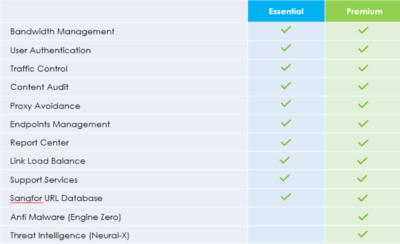
The main difference is Premium Bundle will have all the Essential Bundle components with the addition of Anti-malware protection (Engine Zero) and threat intelligence (Neural-X).