Ideal Applications
- Higher bandwidth IoT & M2M Connectivity & Cloud Trunking
- Multi-site aggregation and concentration
- Link micro-segmentation and tunnel trunking
- WAN Failover & Restore Access Link Protection
- Mid-large Branch data replication cloud connectivity
- MPLS leased-line failover protection
- IP Camera Remote Access VPN and Security
What you should know
- Connect up to 25 remote IpTL appliances and Connect and Extend any Ethernet device over any Dynamic IP Internet with full security
- Start with 1 link and field-expand up to 25 remote links with connection licenses
- Trunk your IoT or M2M devices to your headend applications seamlessly with security and control end-to-end so that your data flows between your devices and applications
- Connects all your devices to both the LAN and the Tunnel so you don’t need extra gear to purchase, configure, & manage
- MPLS or Lease-line redundancy over the Internet with Active/Active redundancy keeping your links up and running and your data flowing without worrying about which path is active
- Load-balance and Link Aggregation supporting up to 64 independent network connections providing true reliable connectivity so you can get the reliability and throughput your applications demand
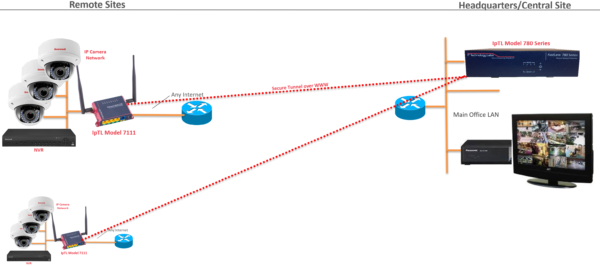
IP Camera to NVR Connectivity
When you have remote IP cameras and NVRs bringing them back to your central site is easy. Using IpTL appliances you can create highly secure and reliable tunnels over any Internet access…including Dynamic IP and behind firewalls.
You’ll get seamless access without issues of NAT traversal issues. For additional security use our exclusive SuperNAC conditional network access control to ensure only your camera has access to your headend.
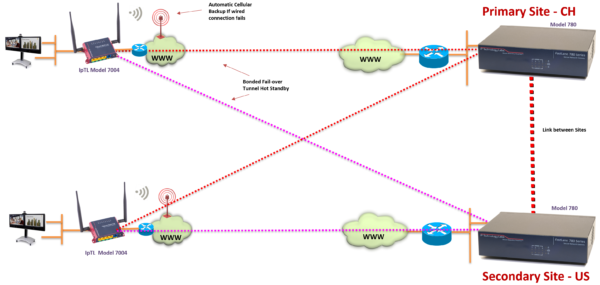
MutiHomed Site-2-Site Full Mesh IoT VPN
IpTL can deliver reliable connectivity and eliminate any single point of failure anywhere in the network. With IpTL you can interconnect your remote site to multiple head-end locations supporting both headquarters and disaster recovery sites at the same time.
Combined with our SystemMonitor™ dynamic path-switching algorithms we ensure secure access to your fielded devices regardless of which physical site you are at.
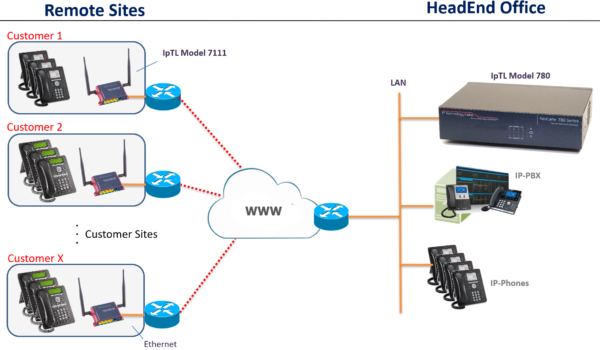
VOIP Extension, Connectivity, & Security
Connect your remote VoIP and UC devices to your central IP-PBX switch without any networking blocks. Operating at L2/Ethernet IpTL “hides” the underlying network – including those that block you like NATs, Dynamic IP, Firewalls, Filters, & Proxys – to give your signaling and media a secure and transparent end-to-end link.
VOIP phones simply DHCP (with their options) from the remote and can even use VLANs across the WAN – try that with your old tired VPN!