Ideal Applications
- IoT & M2M Connectivity, Security, & Cloud Trunking
- WAN Failover & Restore Access Link Protection
- IP Camera Remote Access VPN and Security
- Access Control, IO, Intelligent Readers & Network-based Controllers
- Building Automation Systems HVAC Maintenance, monitoring & control
- Digital Signage Connectivity
- Mobile – Taxis, Light Transport Vehicles
- ATMs, Kiosks, point-of-sale systems, and lottery machines
- Connect and Extend any Ethernet device over any Dynamic IP Internet with full security
- Trunk your IoT or M2M devices to your headend applications seamlessly with security and control end-to-end so that your data flows between your devices and applications
- Wi-Fi can be an Access Point and a Client simultaneously and connects all your devices to both the LAN and the Tunnel so you don’t need extra gear to purchase, configure, & manage
- MPLS or Lease-line redundancy over the Internet with Active/Active redundancy keeps your links up and running and your data flowing without worrying about which path is active
- Load-balance and Link Aggregation supporting up to 64 independent network connections providing true reliable connectivity so you can get the reliability and throughput your applications demand
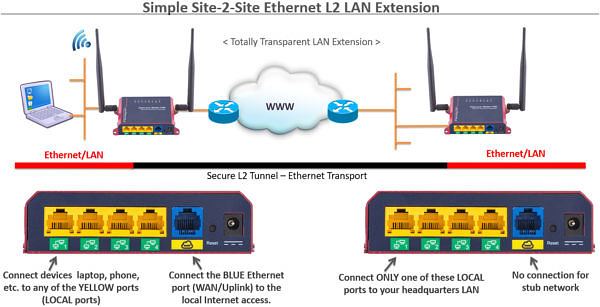
Ethernet Extender over Internet – Simple Site-2-Site Connectivity
IpTL appliances can be used in point-to-point applications for simple Site-2-Site VPNs. Our appliances can transparently extend your LAN from your central location to a remote site. In this case, we look like “The World’s Longest Ethernet Cable™” and your remote devices look and operate “like they are sitting on the LAN.”
Your broadcast, multicast, IPv4, IPv6, UPNP, and mDNS are all preserved. Also, we can connect your non-IP-based network devices — including VLANs, VLAN trunking (e.g. ISL), Modbus-TCP, Profinet/Profibus, CANbus, etc.
Our Patented AutoConnect™ can be used to create this link without requiring ANY configuration of the NAT routers or firewall and will work with Dynamic-IP provider-DHCP addresses on both ends of the link. Wrapped in the latest security, IpTL keeps your good data protected in transit, hides access to your IoT gateway and applications, and keeps the bad guys out.
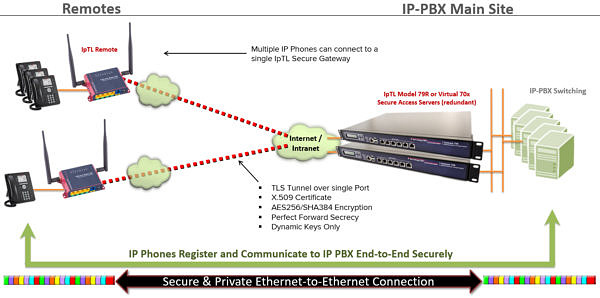
VOIP Extension, Connectivity, & Security
Connect your remote VoIP and UC devices to your central IP-PBX switch without any networking blocks. Operating at L2/Ethernet IpTL “hides” the underlying network – including those that block you like NATs, Dynamic IP, Firewalls, Filters, & Proxys – to give your signaling and media a secure and transparent end-to-end link. VOIP phones can DHCP (with their options) from the remote and even use VLAN across the WAN.
Industrial IoT and M2M Trunking and Backhaul
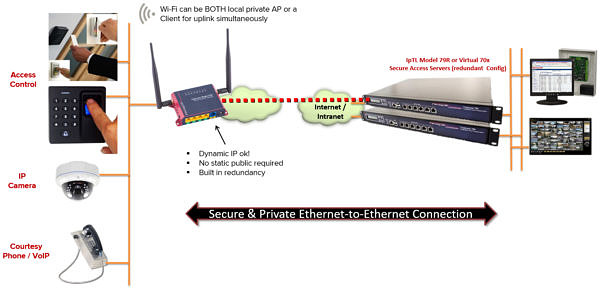
Access control terminals, devices, and cameras are all now network-aware. They are all designed for local installation and work great on the LAN. But how do you truly network these devices to your centralized monitoring, accounting, and analytics?
IpTL’s appliances make it easy work connect your IoT and M2M devices to your remote headquarters or Cloud-based applications. IpTL’s Trunking gives all your IoT gateways & controllers a transparent LAN pipe end-to-end so your applications can communicate without modification.
Wrapped in the latest security, IpTL keeps your good data protected in transit, hides access to your IoT gateway and applications, and keeps the bad guys out.